Day 35: Mastering ConfigMaps and Secrets in Kubernetes🔒🔑🛡️
What is ConfigMaps in K8S?
ConfigMaps are Kubernetes objects that allow you to separate configuration data/files from image content to keep containerized applications portable.
ConfigMaps bind configuration files, command-line arguments, surroundings variables, port numbers, and alternative configuration artifacts to your Pods containers and system parts at run-time.
ConfigMaps are helpful for storing and sharing non-sensitive, unencrypted configuration data. Like Secrets, you’ll be able to produce config maps from files and with yaml declaration.
we can use config maps by relating their name and as a volume.
What are the Secrets in K8S?

Kubernetes Secrets are secure objects which store sensitive data, such as passwords, OAuth tokens, SSH keys, etc. with encryption in your clusters.
Using Secrets gives you more flexibility in a Pod Life cycle definition and control over how sensitive data is used. It reduces the risk of exposing the data to unauthorized users.
Secrets are namespaced objects.
Secrets can be mounted as data volumes or environment variables to be used by a container in a pod.
Secret data is stored in tmpfs in nodes
API server stores secrets as plain text in etcd
A per-secret size limit of 1MB
Task 1:
Create a ConfigMap for your Deployment
Create a ConfigMap for your Deployment using a file or the command line
create a configMap.yaml file

In this example, the apiVersion specifies the version of the Kubernetes API that is being used, and the kind specifies that this is a ConfigMap resource. The metadata section includes information about the ConfigMap, such as its name. The data section is where the key-value pairs are defined.
You can create the ConfigMap by running the following command:
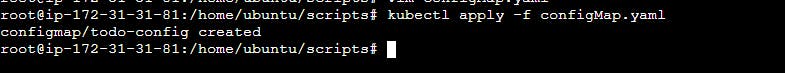
kubectl apply -f configMap.yaml
Update the deployment.yaml file to include the ConfigMap
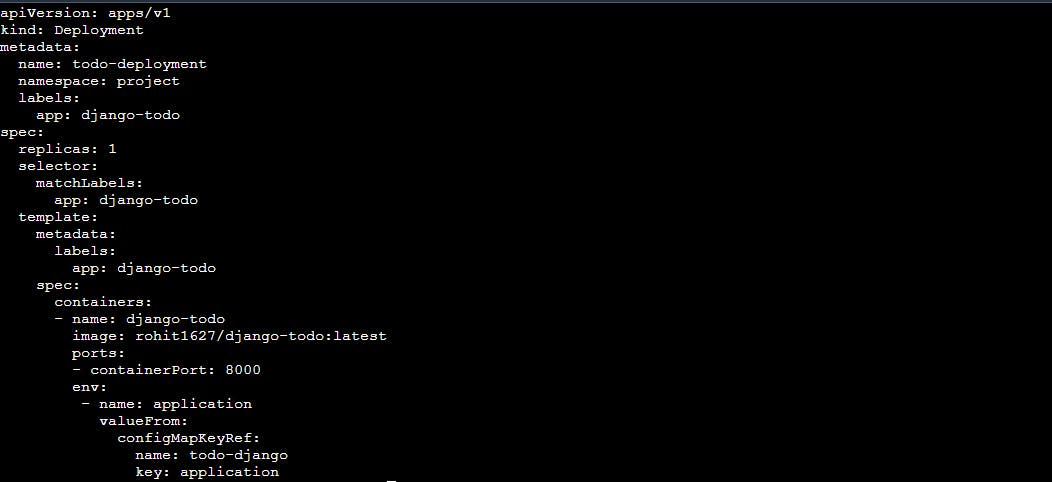
here, the pod definition includes an environment variable application whose value is taken from the ConfigMap. The valueFrom field specifies the source of the value, which is the ConfigMap todo-config and the key application.
Apply the updated deployment using the command:
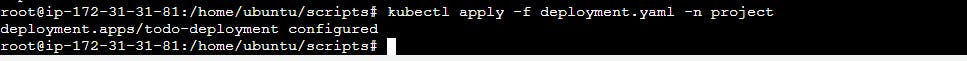
kubectl apply -f deployment.yaml -n <namespace-name>
Verify that the ConfigMap has been created by checking the status of the ConfigMaps in your Namespace.
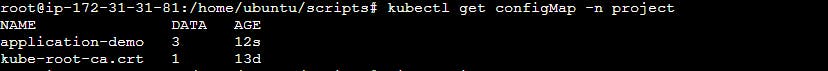
To verify that the ConfigMap has been created, you can use the following command:
This command will display a list of all ConfigMaps in your namespace, along with their status information.
kubectl get configmaps -n <namespace-name>
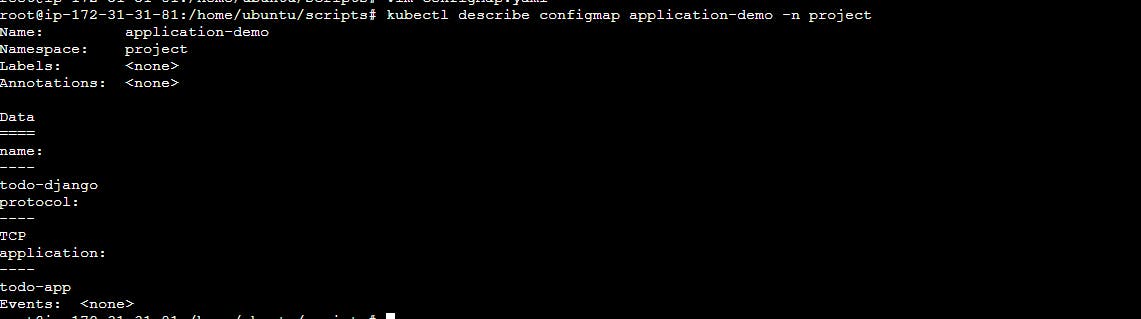
You can also use the following command to view the details of a specific ConfigMap:
This command will display detailed information about the ConfigMap, including its metadata, data, and status.
kubectl describe configmap <configmap-name> -n <namespace-name>
Task 2:
Create a Secret for your Deployment
Create a Secret for your Deployment using a file or the command line
create a secret.yaml file
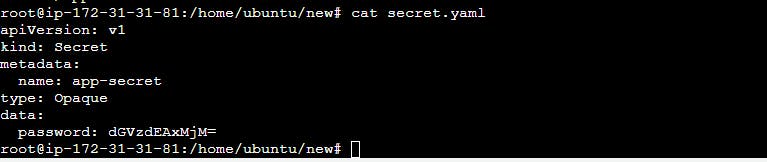
In this example, the apiVersion specifies the version of the Kubernetes API that is being used, and the kind specifies that this is a Secret resource. The metadata section includes information about the Secret, such as its name. The type specifies the type of the Secret, which is Opaque in this case. The data section is where the key-value pairs are defined, with each value being base64 encoded.
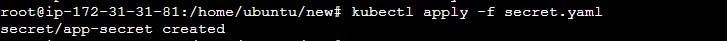
You can create the Secret by running the following command:
kubectl apply -f secret.yaml -n <namespace-name>
Update the deployment.yml file to include the Secret
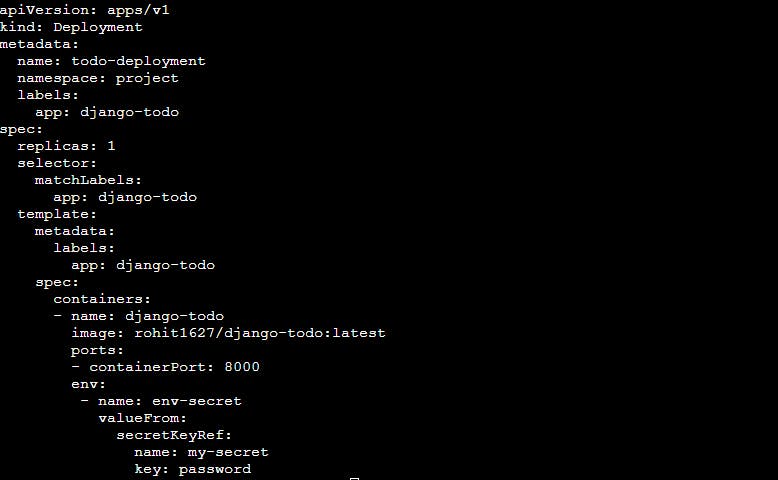
here, the Deployment definition includes an environment variable env-secret whose value is taken from the Secret. The valueFrom field specifies the source of the value, which is the Secret my-secret and the key password
Apply the updated deployment using the command:
kubectl apply -f deployment.yaml -n <namespace-name>
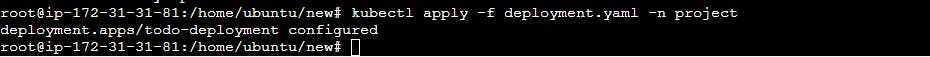
Verify that the Secret has been created by checking the status of the Secrets in your Namespace.
To verify that the Secret has been created, you can use the following command:
kubectl get secrets -n <namespace-name>
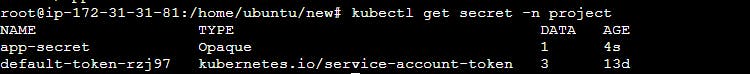
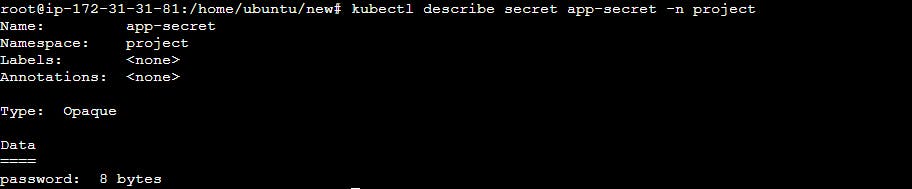
You can also use the following command to view the details of a specific Secret:
kubectl describe secret <secret-name> -n <namespace-name>
Thank you for reading!! I hope you find this article helpful......